March 31, 2018 is World Backup Day. Data is a commodity, but unlike other commodities--it can be replicated without hurting its value. As a result, data backup has become a critical need for the modern business. World Backup Day has been created to remind people to protect their assets by backing up their files.
Tech Minutes
When engaging in business-to-business marketing, your content plays a huge role in your success. Whether you’re creating social media content, blogging, creating articles for your web pages, creating newsletter content, or even working an in-person event, you need to make sure your content is effectively benefitting your marketing.
We’re here to help, so we’ve compiled some key considerations to make as you shape your content marketing strategy through each of the above tactics.
On a day where everybody is Irish, of course we are going to have corned beef, cabbage and potatoes. However, this braised brisket recipe is sure to make you green with envy! Our dessert was mint chocolate chip cookies that were as green as the Emerald Isle! A feast this plentiful, was sure to have made St. Patrick proud. Sláinte, in other words "Cheers!”
Try your luck with the recipes below!
Do you ever decide what to cook based on how many dishes you will dirty in the process?...Well here is your new favorite meal. It not only tastes great, but you only need to dirty one pan, or in Directive’s case, 4 pans! We could not get enough of today’s Crock-Pot Thursday meal, Pepper Jack Chicken and Stuffing.
To try it out yourself with the recipe below!
Considering the recent weather events in the Southern United States, it only seems prudent to address a few considerations that may not be the first to come to mind when making business arrangements for such occurrences. For instance, what are the expectations that employees are held to in the case of a weather disaster?
For the last several years, we have annually asked the members of our team what they were grateful for. It doesn’t have to be a major thing, just some way that technology has improved our everyday lives. After a few silly answers, like memory foam (which is great) and forks (also important technology), they ended up coming up a few great technologies that they are thankful for. Here’s a few stand out items that we wanted to highlight:
Fall is always a great time for cooking, especially in Upstate, NY. Today was a perfect cool day to open up the oven and try a new fall dish. So, for today’s Crock-Pot Thursday we tried; Philly Cheese Steak Bake, Tangy Broccoli Salad, Lemon Butter Roasted Asparagus, and finished off with Lemon Bar Cupcakes. Yum is an understatement. Want to try this meal out for yourself? Check out the recipes below!
Small and medium-sized businesses have increasingly turned to SaaS, or Software as a Service, to access the tools and resources they need to complete their objectives. Rather than maintaining a solution in-house, SaaS is delivered as a web application or through the cloud. However, not all SaaS solutions deliver the same functionality.
Summer isn’t over yet! Today’s Crock-Pot combined a summer favorite, shish kebabs, and a team favorite, fajitas, with: Fajita Shish Kebabs, and Cherry Turnovers for dessert! Watch as our team gives their own unique definition for shish kebabs in today’s video!
Try them for yourself with the recipes below!
If you have an in-house IT specialist, they are very likely the unsung hero of the office. Working behind the scenes to ensure the solutions you rely on are functioning, their efforts also enable you to improve and drive your business forward. However, many technicians can find themselves fighting an uphill battle against overload.
Video can be leveraged to great effect in a wide variety of places, especially on landing pages. In fact, videos have been shown to increase conversions by 86% when used on landing pages. We’ll go over some of the benefits of including videos on your landing pages, and some tips to make these videos even more effective.
Happy National Chili-Dog Day! How lucky are we that such a great holiday fell directly on a Crock-Pot Thursday? Today you’ll watch the techniques of two of our team members in a.....drumroll please........hot dog eating contest! Who will win? Kathy Chupp or Jimmy Mustard? Watch the video to find out!
The concept of deferring to an expert is not new, especially in terms of running a business. If your business encounters a problem in its plumbing, you call in a plumber. When it comes to your business’ IT solutions, there are professionals who can help with issues there as well: IT consultants.
After a year like 2016, it should come as no surprise that 2017 has been a year of significant cyber threats. Looking back on the events of the year so far may help us to anticipate what kind of threats we can anticipate in the second half of 2017.
Your server is an integral part of your IT setup, which means that it is all the more crucial that it is managed properly. As the central hub of your network, it connects all of the devices that you rely on to each other, allowing them to interact and communicate. Under proper server management practices, your server will be more able to accomplish this task.
In order to better understand how to properly approach server management, it helps to look at it not as an entire process, but to break it into its two parts.
It should come as no surprise that a crash occurring in your computer network is a bad thing for your business. However, the real ramifications of such an event might not immediately come to mind. Fortunately, there are precautions that may be put into place that can help you to mitigate the chances of a network crash.
Patrons of Chipotle Mexican Grill might soon start to feel sick to their stomach, but it will have nothing to do with the food--the company has disclosed the full list of upstate New York restaurants affected by the point-of-sale malware that infected the company between March 24th and April 18th of this year. Could this breach have compromised one of your cards? Could you be vulnerable in some other ways, too?
On behalf of everyone here at Directive, we wanted to acknowledge the video that was released a few weeks ago that claims we grow our Crock-Pot Thursday meals in what we said was our pizza orchard. These claims were not entirely accurate. See the video.
There’s a pretty good chance that you’ve seen us throw the term BDR around quite a bit, or reference what we have in place as far as a Backup and DIsaster Recovery solution is concerned. However, do you know what we’re really talking about when we toss out this industry jargon?
 Uh oh, your PC or laptop is starting to act up again. If it’s been checked for software problems, you’re most likely dealing with an issue with the hardware. Looks like it's time for a trip to the repair shop--but before you go, you need to make a few preparations. Here are the five things you need to consider before taking your computer in for repair.
Uh oh, your PC or laptop is starting to act up again. If it’s been checked for software problems, you’re most likely dealing with an issue with the hardware. Looks like it's time for a trip to the repair shop--but before you go, you need to make a few preparations. Here are the five things you need to consider before taking your computer in for repair.
 In November of 2016, Governor of New York Andrew Cuomo devoted $30 million dollars to a 50-mile-long flight traffic management system to promote the use of unmanned aircraft systems (more commonly known as drones) for Central New York business purposes. This ‘corridor,’ as it is called, will stretch from Griffiss Air Force Base in Rome to Syracuse by sometime in 2018.
In November of 2016, Governor of New York Andrew Cuomo devoted $30 million dollars to a 50-mile-long flight traffic management system to promote the use of unmanned aircraft systems (more commonly known as drones) for Central New York business purposes. This ‘corridor,’ as it is called, will stretch from Griffiss Air Force Base in Rome to Syracuse by sometime in 2018.
 There are an unfortunate number of cyber threats out there; protecting your company’s network from these threats is paramount. In order to find out how acquainted you are with the malicious programs and attacks that could harm your business, we’ve devised this quick quiz to test your knowledge.
There are an unfortunate number of cyber threats out there; protecting your company’s network from these threats is paramount. In order to find out how acquainted you are with the malicious programs and attacks that could harm your business, we’ve devised this quick quiz to test your knowledge.
 Doing business in this day and age depends more and more on your ability to connect to the Internet. It is also essential that your connectivity speeds are able to keep up with your business needs. For many operating in New York State, this has been a problem, but no longer.
Doing business in this day and age depends more and more on your ability to connect to the Internet. It is also essential that your connectivity speeds are able to keep up with your business needs. For many operating in New York State, this has been a problem, but no longer.
 In February, the New York State Office of the Attorney General filed a lawsuit against Spectrum-Time Warner Cable and its parent company, Charter Communications, alleging that the company has been systematically defrauding customers since 2012 by promising and charging for Internet speeds that it knew it couldn’t offer. This case of fraud raises an important question, “How do you know if you’re really getting the Internet speed you’re paying for?”
In February, the New York State Office of the Attorney General filed a lawsuit against Spectrum-Time Warner Cable and its parent company, Charter Communications, alleging that the company has been systematically defrauding customers since 2012 by promising and charging for Internet speeds that it knew it couldn’t offer. This case of fraud raises an important question, “How do you know if you’re really getting the Internet speed you’re paying for?”
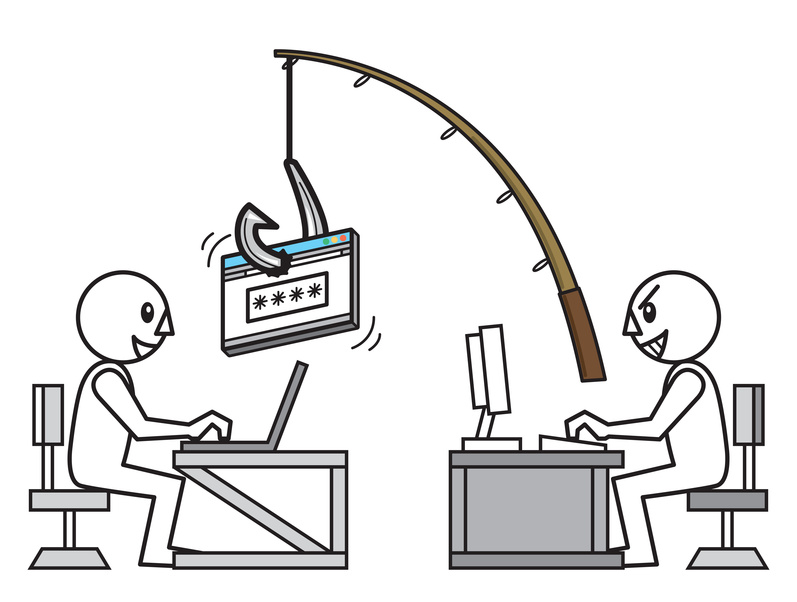 Small businesses today have a lot more to worry about than they did twenty, or even ten years ago. Threats have grown so sophisticated that it can be difficult to gauge just how vulnerable your organization is to them. It’s especially important that your organization protects itself from the dangers that lurk within emails, tucked behind thinly-veiled schemes and honeyed words.
Small businesses today have a lot more to worry about than they did twenty, or even ten years ago. Threats have grown so sophisticated that it can be difficult to gauge just how vulnerable your organization is to them. It’s especially important that your organization protects itself from the dangers that lurk within emails, tucked behind thinly-veiled schemes and honeyed words.
Every year, we hear about a major corporation being hacked. No matter the size of the business, weak links can always be identified in a network’s security. Let’s investigate some of the biggest security leaks and how they could’ve been avoided. In one case, it was as easy as implementing two-factor authentication.
By now, you've heard about the many advantages of hosting your data and applications in the cloud. To take advantage of these money-saving benefits, you'll want to select the right cloud provider to host and manage your data. Otherwise, you may end up with poor support and disappointing service.
To help you pick the right hosting provider, you first need to familiarize yourself with your options. Here's a walkthrough of what you need to look for.
In a historically large media merge, AT&T and Time Warner have come to an agreement in a proposal that has been discussed since as early as August 2016. The wireless provider intends to purchase Time Warner’s media holdings for a whopping total of $85.4 billion in cash and stocks, assuming the merger passes the inspection of antitrust regulators.
Part 4 of 7 - Determining Your Facebook Advertising Budget [Series]
In the first part of this series, you may remember us discussing the affordability Facebook offers businesses. In fact, that is one of the many reasons Facebook advertising has become so successful. Any budget can be supported, but how far can your budget take you?
Part 3 of 7 - Creating an Ad [Series]
Facebook Ads have the ability to transform your company and dramatically increase your leads without destroying your budget. If you want to reach 1.55 billion Facebook users that could potentially turn into your clients, then Facebook Advertising is right for you. The following will tell you the preliminary steps you need to know to create a Facebook Advertisement of your very own!
Lately, I have come across articles from friends and peers that have discussed a topic and presented inaccuracies that I find troublesome. There is some confusion that syndicated content is never worthy of respect or consideration. This seems especially true when it is compared to custom content. However, this may not always be the case, and so there are a few points that need to be cleared up from the get-go. Considering that my company provides syndicated, custom, and SEO content, I am an authority uniquely positioned to clarify this matter, which is what I intend to do here.
Since the invention of laptops, “the workplace” has become a phrase that may describe many more places than the office your business is established in, as mobile computers encourage taking your productivity with you by their very nature. However, this “productivity anywhere” feature does not come without its dangers to the poor laptop.
Time hasn’t been kind to the password. It’s continuously put down as one of the least secure methods of protecting systems. It’s not due to any fault of the password, though. People just have a hard time remembering long and complex passwords. To aid in security, it’s recommended that you use some sort of multi-factor authentication. While some users prefer easy SMS message two-factor authentication, there are actually many different types of multi-factor authentication available.
 When you think about the stock market, one vibrant image that comes to mind is the chaotic trading floor of the New York Stock Exchange, with traders climbing over each other and barking orders. Today, the NYSE trading floor is much more subdued, a testimony to just how much technology has changed the financial marketplace.
When you think about the stock market, one vibrant image that comes to mind is the chaotic trading floor of the New York Stock Exchange, with traders climbing over each other and barking orders. Today, the NYSE trading floor is much more subdued, a testimony to just how much technology has changed the financial marketplace.
 Properly maintained IT security is necessary for the modern business. If your business utilizes email, connects to the Internet, or has employees that use mobile devices like smartphones and tablets, you need to have solid IT security in place. The following covers a lot of common elements required to protect your data and reputation. Keep in mind, depending on your industry, there may be additional compliances and regulations you need to follow.
Properly maintained IT security is necessary for the modern business. If your business utilizes email, connects to the Internet, or has employees that use mobile devices like smartphones and tablets, you need to have solid IT security in place. The following covers a lot of common elements required to protect your data and reputation. Keep in mind, depending on your industry, there may be additional compliances and regulations you need to follow.
 Although successful business owners are often cut from different cloths, one factor that many share is constantly measuring and assessing everything involving your business. From the profitability of particular departments, to equipment lifecycles, to the various expenses your company pays each month, the key to sustainable growth is by understanding what works and what doesn’t.
Although successful business owners are often cut from different cloths, one factor that many share is constantly measuring and assessing everything involving your business. From the profitability of particular departments, to equipment lifecycles, to the various expenses your company pays each month, the key to sustainable growth is by understanding what works and what doesn’t.
 When it feels like everybody is out to get you, there's only one way to survive: Trust nobody. You may not have too many physical enemies ready to jump you, but there's an army of hackers wanting to breach your company's database. One of the securest ways to keep your company's information safe is to implement a "zero trust" network security model.
When it feels like everybody is out to get you, there's only one way to survive: Trust nobody. You may not have too many physical enemies ready to jump you, but there's an army of hackers wanting to breach your company's database. One of the securest ways to keep your company's information safe is to implement a "zero trust" network security model.
 When your business is in need of IT assistance, you want to make sure that you are getting the best of the best. However, the best course of action isn't to just look at someone's qualifications. You also want to look at their personality and other characteristics which can tell you a lot about who you are hiring.
When your business is in need of IT assistance, you want to make sure that you are getting the best of the best. However, the best course of action isn't to just look at someone's qualifications. You also want to look at their personality and other characteristics which can tell you a lot about who you are hiring.
 Everybody loves their freedom, but for some, freedom is an illusion. Take for example the busy business owner. Often times, their work schedules are so packed with tasks that they don't feel free to take a break and enjoy themselves. Technically, they have the freedom to quit, but we think there's a better way to find freedom in the workplace!
Everybody loves their freedom, but for some, freedom is an illusion. Take for example the busy business owner. Often times, their work schedules are so packed with tasks that they don't feel free to take a break and enjoy themselves. Technically, they have the freedom to quit, but we think there's a better way to find freedom in the workplace!
 Everything seems to be going your way for once. The office is really coming together to make that big business deal you've been trying so hard to get for months. You shake the CEO's hand and seal the deal. You stroll out of the office with a spring in your step and get in the taxi to head home for the night. But the cab driver is playing loud music - so loud that it just sounds like screeching in your ear. And then you wake up, your alarm clock ringing at max volume. It's 7:00am, and it's time to go back to the office that feels like a prison, and your employees the inmates.
Everything seems to be going your way for once. The office is really coming together to make that big business deal you've been trying so hard to get for months. You shake the CEO's hand and seal the deal. You stroll out of the office with a spring in your step and get in the taxi to head home for the night. But the cab driver is playing loud music - so loud that it just sounds like screeching in your ear. And then you wake up, your alarm clock ringing at max volume. It's 7:00am, and it's time to go back to the office that feels like a prison, and your employees the inmates.
 The technology for artificial intelligence isn't quite there yet, but according to a recent Turing Test performed at the University of Reading, there might be some hope for it in the near future. A Russian team has assembled a computer program called Eugene Goostman who many believe is the first to pass the Turing Test.
The technology for artificial intelligence isn't quite there yet, but according to a recent Turing Test performed at the University of Reading, there might be some hope for it in the near future. A Russian team has assembled a computer program called Eugene Goostman who many believe is the first to pass the Turing Test.
 Everybody knows operating a computer under cooler temperatures increases its performance. This is why some server closets feel like a walk-in refrigerator. One thing about computers that you may not have known is whether or not running a PC at cooler temperatures extends its life. Logically, one would assume yes, however, the research says otherwise.
Everybody knows operating a computer under cooler temperatures increases its performance. This is why some server closets feel like a walk-in refrigerator. One thing about computers that you may not have known is whether or not running a PC at cooler temperatures extends its life. Logically, one would assume yes, however, the research says otherwise.
 For the past decade, touch-screens have changed the way that we as a society touch technology, and have greatly increased the mobility of business in that short time. This trend started with the smartphone, then spread to the 10-inch tablet and larger tablets - perfect for watching YouTube videos, Netflix, or other media consumption.
For the past decade, touch-screens have changed the way that we as a society touch technology, and have greatly increased the mobility of business in that short time. This trend started with the smartphone, then spread to the 10-inch tablet and larger tablets - perfect for watching YouTube videos, Netflix, or other media consumption.
 Wearable technology is still relatively new. While technologies like Google Glass have found enthusiastic users, in the eyes of the general public, the verdict is still out. The best thing a Google Glass user can do with their favorite new tech is to use it responsibly. Here's some tips on how to be a good AmGlassador!
Wearable technology is still relatively new. While technologies like Google Glass have found enthusiastic users, in the eyes of the general public, the verdict is still out. The best thing a Google Glass user can do with their favorite new tech is to use it responsibly. Here's some tips on how to be a good AmGlassador!
 It has been two weeks since the National Communications Association warned the world about the GameOver Zeus and Cryptolocker ransomware, and if you haven't taken steps to avoid these threats, it's not too late - if you haven't been infected yet, do so as soon as possible. Otherwise, your network will be vulnerable, and so will your banking credentials.
It has been two weeks since the National Communications Association warned the world about the GameOver Zeus and Cryptolocker ransomware, and if you haven't taken steps to avoid these threats, it's not too late - if you haven't been infected yet, do so as soon as possible. Otherwise, your network will be vulnerable, and so will your banking credentials.
 Whether you're watching the World Cup or going on a business trip overseas, you will experience foreign cultures and run into what's known as "the language barrier." Thanks to technology, you can quickly and easily make sense of World Cup statistics, or make your way around a city where English isn't the norm.
Whether you're watching the World Cup or going on a business trip overseas, you will experience foreign cultures and run into what's known as "the language barrier." Thanks to technology, you can quickly and easily make sense of World Cup statistics, or make your way around a city where English isn't the norm.
 Does your company have dedicated antivirus software to protect it against the annoying threats on the Internet? Sometimes, a computer virus can weasel its way past your software, but there's no greater frustration than when you realize that the reason you contracted a virus is because an employee disabled your software. Don't let this happen to you!
Does your company have dedicated antivirus software to protect it against the annoying threats on the Internet? Sometimes, a computer virus can weasel its way past your software, but there's no greater frustration than when you realize that the reason you contracted a virus is because an employee disabled your software. Don't let this happen to you!
 Whether you're on the move or at the workplace, your WiFi connection isn't the most secure method of browsing the Internet. Hacking techniques are growing more sophisticated, and you never know who could be observing your connection and Internet activity. Thankfully, there are ways to remediate this issue, like using a Virtual Private Network (VPN).
Whether you're on the move or at the workplace, your WiFi connection isn't the most secure method of browsing the Internet. Hacking techniques are growing more sophisticated, and you never know who could be observing your connection and Internet activity. Thankfully, there are ways to remediate this issue, like using a Virtual Private Network (VPN).
 In this day and age, your company's data is extremely important. Without it, your company would likely cease to exist. But, it's not just you - the entire world is this way, and the more information that's out there, the more storage and backup that is needed. Professionals are constantly looking for ways to expand the way we store data, and last month, Sony managed to discover something entirely new that may change the way that we store our information.
In this day and age, your company's data is extremely important. Without it, your company would likely cease to exist. But, it's not just you - the entire world is this way, and the more information that's out there, the more storage and backup that is needed. Professionals are constantly looking for ways to expand the way we store data, and last month, Sony managed to discover something entirely new that may change the way that we store our information.
 Take a moment to consider your answer to this question, "What would you do if all of your business's data was somehow lost overnight?" How would you react, and what would you do about it? Your data is valuable, so much in fact that your business would be lost without it, and likely wouldn't be able to run properly.
Take a moment to consider your answer to this question, "What would you do if all of your business's data was somehow lost overnight?" How would you react, and what would you do about it? Your data is valuable, so much in fact that your business would be lost without it, and likely wouldn't be able to run properly.
 The Internet is a vast ocean filled with all sorts of different creatures. Many are harmless, like the bottlenose dolphin, but once in a while you will encounter an aggressive shark. But no matter how powerful or intelligent these creatures are, they still wind up flopping around on the deck of some fisherman's boat. Why? Because fishermen know what they're looking for and how to capture it. The same can be said about Internet phishers.
The Internet is a vast ocean filled with all sorts of different creatures. Many are harmless, like the bottlenose dolphin, but once in a while you will encounter an aggressive shark. But no matter how powerful or intelligent these creatures are, they still wind up flopping around on the deck of some fisherman's boat. Why? Because fishermen know what they're looking for and how to capture it. The same can be said about Internet phishers.
 On May 7, 2014, the U.S. Securities and Exchange Commission (SEC) released a news alert declaring Bitcoin, and all other virtual currencies insecure and unsafe. Due to a rise in Bitcoin popularity, many investors and business owners like to use it for worldwide transactions. But, how safe is it, and how likely are you to run into a Bitcoin fraud scheme?
On May 7, 2014, the U.S. Securities and Exchange Commission (SEC) released a news alert declaring Bitcoin, and all other virtual currencies insecure and unsafe. Due to a rise in Bitcoin popularity, many investors and business owners like to use it for worldwide transactions. But, how safe is it, and how likely are you to run into a Bitcoin fraud scheme?
 In December 2013, retail superpower Target was the target (hehe) of a massive data breach that could have affected as many as 110 million customers. On Monday, May 5, 2014, the CEO of Target, Gregg Steinhafel, announced that he would be stepping down, no doubt a result of the chaos that engulfed his company in the aftermath of this data breach. Target's CFO, John Mulligan, has stepped in as interim CEO until the position is filled once again.
In December 2013, retail superpower Target was the target (hehe) of a massive data breach that could have affected as many as 110 million customers. On Monday, May 5, 2014, the CEO of Target, Gregg Steinhafel, announced that he would be stepping down, no doubt a result of the chaos that engulfed his company in the aftermath of this data breach. Target's CFO, John Mulligan, has stepped in as interim CEO until the position is filled once again.
 Microsoft has changed its tune recently. They have made a serious push to take advantage in the mobile computing explosion by creating software that is designed specifically for the mobile device user. When the software giant released Windows Phone 8 in the fourth quarter of 2012, many thought it was only a matter of time before the software would resonate with mobile users. Unfortunately for Microsoft, the smartphone market hasn't been as friendly as the home and business computing market, and Windows Phone 8 has been a thorough disappointment.
Microsoft has changed its tune recently. They have made a serious push to take advantage in the mobile computing explosion by creating software that is designed specifically for the mobile device user. When the software giant released Windows Phone 8 in the fourth quarter of 2012, many thought it was only a matter of time before the software would resonate with mobile users. Unfortunately for Microsoft, the smartphone market hasn't been as friendly as the home and business computing market, and Windows Phone 8 has been a thorough disappointment.
 A new botnet threat could spell "game over" for unaware Windows users - the threat targets almost all versions of Windows and Windows Server (excluding Windows 8.1). Even though the Department of Homeland Security, Federal Bureau of Investigation, and Department of Justice have disrupted it, users are still at risk. Thankfully, they still have time - two weeks, until the threat returns.
A new botnet threat could spell "game over" for unaware Windows users - the threat targets almost all versions of Windows and Windows Server (excluding Windows 8.1). Even though the Department of Homeland Security, Federal Bureau of Investigation, and Department of Justice have disrupted it, users are still at risk. Thankfully, they still have time - two weeks, until the threat returns.
 Spell check makes spelling super easy. All you have to do is regurgitate a string of letters that halfway sound like the word you're thinking of and the red squiggly line will take care of the rest. Admittedly, spellcheck has turned most of us into lazy spellers, which is why it's crucial that your spell check settings are adjusted properly when using Microsoft Publisher.
Spell check makes spelling super easy. All you have to do is regurgitate a string of letters that halfway sound like the word you're thinking of and the red squiggly line will take care of the rest. Admittedly, spellcheck has turned most of us into lazy spellers, which is why it's crucial that your spell check settings are adjusted properly when using Microsoft Publisher.
 Mobile devices are designed for different purposes than the big, bulky desktops are. The Chrome operating system of the Google Chromebook is a perfect example of this - it looks like nothing but a browser with a keyboard. Sure, it can't do everything a real computer can do, but it sure can do a lot more than some people give it credit for.
Mobile devices are designed for different purposes than the big, bulky desktops are. The Chrome operating system of the Google Chromebook is a perfect example of this - it looks like nothing but a browser with a keyboard. Sure, it can't do everything a real computer can do, but it sure can do a lot more than some people give it credit for.
 We all know about the cryptocurrency Bitcoin, but do you know about Dogecoin? Its figurehead, the grammatically-challenged Shiba Inu, quickly became an Internet sensation called the Doge meme, and was adopted as the mascot for Dogecoin. However, before you go out and buy yourself some Dogecoin for you and your buddies, you should know that its database, the Doge Vault, has been hacked.
We all know about the cryptocurrency Bitcoin, but do you know about Dogecoin? Its figurehead, the grammatically-challenged Shiba Inu, quickly became an Internet sensation called the Doge meme, and was adopted as the mascot for Dogecoin. However, before you go out and buy yourself some Dogecoin for you and your buddies, you should know that its database, the Doge Vault, has been hacked.
 Firewalls are the first thing companies think of when it comes to data security. What is the last security risk on an organization's mind? Your most tech-savvy employee. If someone were to "get to" the employee overseeing your network, they would be able to do some serious damage. What are you doing to protect your data from the employees you trust the most?
Firewalls are the first thing companies think of when it comes to data security. What is the last security risk on an organization's mind? Your most tech-savvy employee. If someone were to "get to" the employee overseeing your network, they would be able to do some serious damage. What are you doing to protect your data from the employees you trust the most?
 Many people often associate the coming of spring with spring cleaning, or giving their house a good frisking. They use this opportunity to get rid of all of the junk they don't need anymore, such as useless wedding gifts or things they haven't touched, let alone seen, in years. The same thing can be done with your IT department at the workplace.
Many people often associate the coming of spring with spring cleaning, or giving their house a good frisking. They use this opportunity to get rid of all of the junk they don't need anymore, such as useless wedding gifts or things they haven't touched, let alone seen, in years. The same thing can be done with your IT department at the workplace.
 Many websites around the world are still suffering from the nasty little bug called Heartbleed that we covered last month. This prompted over 30,000 TLS/SSL certificates to be revoked and reissued, but many of them were reissued with the same keys. If this was going to happen, why revoke and reissue them in the first place? They're still just as vulnerable as before, since Heartbleed could have leaked those same keys weeks ago.
Many websites around the world are still suffering from the nasty little bug called Heartbleed that we covered last month. This prompted over 30,000 TLS/SSL certificates to be revoked and reissued, but many of them were reissued with the same keys. If this was going to happen, why revoke and reissue them in the first place? They're still just as vulnerable as before, since Heartbleed could have leaked those same keys weeks ago.
 When it comes to productivity, the latest technology can be a huge boon. A proper word processor can increase your productivity drastically if you know how to use it. However, one of today's most ingenious writers - George R. R. Martin - is still stuck in the Stone Age of word processing technology!
When it comes to productivity, the latest technology can be a huge boon. A proper word processor can increase your productivity drastically if you know how to use it. However, one of today's most ingenious writers - George R. R. Martin - is still stuck in the Stone Age of word processing technology!
 eBay issued an official declaration on Wednesday, May 21, 2014 that one of its databases had been hacked. The worst part? This database, which housed users' passwords, was compromised. But, there is a silver lining to all of this - no information has been stolen.
eBay issued an official declaration on Wednesday, May 21, 2014 that one of its databases had been hacked. The worst part? This database, which housed users' passwords, was compromised. But, there is a silver lining to all of this - no information has been stolen.
None that they know of, anyway. The auctioning website is still cautioning users to change their passwords in light of the attack.
 In light of all of the recent vulnerabilities found in Microsoft's Internet Explorer browser and Windows XP operating system, owners of XP are growing nervous about the upcoming "patch Tuesday," Microsoft's monthly patch release day. But, what if what Microsoft isn't patching in the newer operating systems is what needs to be patched the most in XP?
In light of all of the recent vulnerabilities found in Microsoft's Internet Explorer browser and Windows XP operating system, owners of XP are growing nervous about the upcoming "patch Tuesday," Microsoft's monthly patch release day. But, what if what Microsoft isn't patching in the newer operating systems is what needs to be patched the most in XP?
 How much paper and ink does your company use every week? Every month? Every year? More importantly, how much does this wind up costing your company in the long run? According to a study by 14 year-old science fair wiz Suvir Mirchandani, it was discovered that his Pittsburgh-area school district could reduce ink consumption by 24 percent and save an average of $21,000 a year by simply switching fonts. That's half of what the average American's annual salary is!
How much paper and ink does your company use every week? Every month? Every year? More importantly, how much does this wind up costing your company in the long run? According to a study by 14 year-old science fair wiz Suvir Mirchandani, it was discovered that his Pittsburgh-area school district could reduce ink consumption by 24 percent and save an average of $21,000 a year by simply switching fonts. That's half of what the average American's annual salary is!
 In our previous blog article, we introduced you to Chris Dancy, aka "The Most Connected Human on Earth." We told you Chris' story, how the former IT manager lost his job due to corporate downsizing and then turned to quantitative technology to find relevance in an ever-changing work environment. Today, Chris utilizes hundreds of different technologies and systems as part of his "quantitative life existence." In part two of our interview with Chris, he explains how you too can be a connected human.
In our previous blog article, we introduced you to Chris Dancy, aka "The Most Connected Human on Earth." We told you Chris' story, how the former IT manager lost his job due to corporate downsizing and then turned to quantitative technology to find relevance in an ever-changing work environment. Today, Chris utilizes hundreds of different technologies and systems as part of his "quantitative life existence." In part two of our interview with Chris, he explains how you too can be a connected human.
 If your workplace is filled with computers, you likely experience a number of eye-straining problems related to your technology. According to All About Vision, symptoms of computer eye strain impair 50-to-90 percent of all computer workers. That's a pretty good-sized chunk of your employees, and they probably don't enjoy any of these symptoms, including physical fatigue, decreased productivity, and even increased error rate.
If your workplace is filled with computers, you likely experience a number of eye-straining problems related to your technology. According to All About Vision, symptoms of computer eye strain impair 50-to-90 percent of all computer workers. That's a pretty good-sized chunk of your employees, and they probably don't enjoy any of these symptoms, including physical fatigue, decreased productivity, and even increased error rate.
 Who's in charge of making the decisions in your business concerning technology? Ideally, you want an internal IT manager or a CIO with IT experience calling the tech shots. However, many businesses don't have this luxury. According to a CompTIA survey from last November, 48 percent of businesses have managers making decisions about technology implementation that don't have IT experience.
Who's in charge of making the decisions in your business concerning technology? Ideally, you want an internal IT manager or a CIO with IT experience calling the tech shots. However, many businesses don't have this luxury. According to a CompTIA survey from last November, 48 percent of businesses have managers making decisions about technology implementation that don't have IT experience.
 Microsoft stated weeks ago that they would no longer support Windows 8.1, unless the operating system was updated to Windows 8.1 Update by May 13th. But one day before the deadline, Microsoft announced they have pushed the deadline back substantially. This update is crucial if you desire to continue receiving patches and updates from the company. Which you should!
Microsoft stated weeks ago that they would no longer support Windows 8.1, unless the operating system was updated to Windows 8.1 Update by May 13th. But one day before the deadline, Microsoft announced they have pushed the deadline back substantially. This update is crucial if you desire to continue receiving patches and updates from the company. Which you should!
 Let's face it, no matter how quickly you can type, there is only so much you can accomplish without the use of keyboard shortcuts. Perhaps you never cared to learn them, or maybe you never had the opportunity. Now that you own a small business, your productivity and efficiency is at stake. Thankfully, some of the most useful shortcuts utilize one common key: the Control key.
Let's face it, no matter how quickly you can type, there is only so much you can accomplish without the use of keyboard shortcuts. Perhaps you never cared to learn them, or maybe you never had the opportunity. Now that you own a small business, your productivity and efficiency is at stake. Thankfully, some of the most useful shortcuts utilize one common key: the Control key.
 Most people think of Microsoft Word as a normal word processor, and to an extent, that's exactly what it is. But did you know that Word 2013 has a built-in citation mechanism for your research needs? Say you are writing a white paper for marketing use, and you took specific statistics from a website. You want to make sure you cite these facts. Why? Because if you cite them, it makes your business look professional, and it looks good when you know how to credit someone else's work.
Most people think of Microsoft Word as a normal word processor, and to an extent, that's exactly what it is. But did you know that Word 2013 has a built-in citation mechanism for your research needs? Say you are writing a white paper for marketing use, and you took specific statistics from a website. You want to make sure you cite these facts. Why? Because if you cite them, it makes your business look professional, and it looks good when you know how to credit someone else's work.
 You've just started your own small business, and your head is swimming with ideas that you want to share with the entire world. You create a blog and publish a few articles, but only get a few hits. You sigh, write another entry, and then shut down your computer for the night. This happens for a few days, which turn into weeks, and months, and something doesn't feel right to you. Why aren't you getting any viewers?
You've just started your own small business, and your head is swimming with ideas that you want to share with the entire world. You create a blog and publish a few articles, but only get a few hits. You sigh, write another entry, and then shut down your computer for the night. This happens for a few days, which turn into weeks, and months, and something doesn't feel right to you. Why aren't you getting any viewers?
 In today's connected home, Internet security needs to extend beyond the PC. Any device that's connected to the Internet needs to be password protected, secured with a firewall, and utilize available security apps. These precautions should be taken even with seemingly harmless devices like baby monitors. A family from Ohio recently learned this lesson the hard way.
In today's connected home, Internet security needs to extend beyond the PC. Any device that's connected to the Internet needs to be password protected, secured with a firewall, and utilize available security apps. These precautions should be taken even with seemingly harmless devices like baby monitors. A family from Ohio recently learned this lesson the hard way.
 Microsoft put out the fire from the zero-day bug affecting users of its popular web browser Internet Explorer by releasing a security patch. This IE bug is a bad one that allows hackers to take over a PC. The patch was released on May 1st and if you haven't yet applied it to your PC, then you should do so right away!
Microsoft put out the fire from the zero-day bug affecting users of its popular web browser Internet Explorer by releasing a security patch. This IE bug is a bad one that allows hackers to take over a PC. The patch was released on May 1st and if you haven't yet applied it to your PC, then you should do so right away!
 Your mind is racing at a mile a minute, and you keep a to-do list for all of the things you are supposed to do. Unfortunately, that to-do list is often forgotten about. You save it as a .DOC text file on your computer, which has been making a strange clicking noise lately. But one day, the clicking sound gets worse, and worse, and worse, until your computer stops working completely. Just like that, all of your data is gone, and that's when it hits you.
Your mind is racing at a mile a minute, and you keep a to-do list for all of the things you are supposed to do. Unfortunately, that to-do list is often forgotten about. You save it as a .DOC text file on your computer, which has been making a strange clicking noise lately. But one day, the clicking sound gets worse, and worse, and worse, until your computer stops working completely. Just like that, all of your data is gone, and that's when it hits you.
 On May 4th you may see more Star Wars T-shirts than normal. This is because May 4th is recognized around the galaxy as Star Wars Day (May the 4th be with you). Thanks to the abundant use of technology throughout this science fiction franchise, you can bet your podracer that we can find an IT lesson from Star Wars that can help your business!
On May 4th you may see more Star Wars T-shirts than normal. This is because May 4th is recognized around the galaxy as Star Wars Day (May the 4th be with you). Thanks to the abundant use of technology throughout this science fiction franchise, you can bet your podracer that we can find an IT lesson from Star Wars that can help your business!
 Across the galaxy, Star Wars fans will be celebrating their beloved science fiction franchise on May 4th (May the fourth be with you). One of the most fascinating aspects about Star Wars is its space technology. As cool as lightsabers and blasters are, Star Wars tech can break down just like our modern space technology. Concerning technology repair, we think troubleshooting space tech in our day can be just as exciting as repairing space technology "a long time ago in a galaxy far, far away."
Across the galaxy, Star Wars fans will be celebrating their beloved science fiction franchise on May 4th (May the fourth be with you). One of the most fascinating aspects about Star Wars is its space technology. As cool as lightsabers and blasters are, Star Wars tech can break down just like our modern space technology. Concerning technology repair, we think troubleshooting space tech in our day can be just as exciting as repairing space technology "a long time ago in a galaxy far, far away."
 If we told you that a battery's performance decreases as time goes on, how many of you would be surprised? The same goes for anything. Nothing lasts forever, and batteries are no different. However, there are ways you can increase the lifespan of your laptop's battery. Portable technology is important for your business, and a good, strong laptop battery is necessary.
If we told you that a battery's performance decreases as time goes on, how many of you would be surprised? The same goes for anything. Nothing lasts forever, and batteries are no different. However, there are ways you can increase the lifespan of your laptop's battery. Portable technology is important for your business, and a good, strong laptop battery is necessary.
 Well, that didn't take long. Eight months ago Microsoft released Windows 8.1 and now they're sounding the alarm that users better comply and install the latest updates or lose security support from Microsoft. What makes this news peculiar is that it took 12 years for Microsoft to reach the same verdict with its popular Windows XP operating system. What gives, Microsoft?
Well, that didn't take long. Eight months ago Microsoft released Windows 8.1 and now they're sounding the alarm that users better comply and install the latest updates or lose security support from Microsoft. What makes this news peculiar is that it took 12 years for Microsoft to reach the same verdict with its popular Windows XP operating system. What gives, Microsoft?
 A lot of people use Google Chrome or Firefox as their browser of choice, and it's easy to see why. They are updated constantly and have great features. However, a lot of people still stick to what they know and love - Internet Explorer. There are a lot of people out there that still use this browser, and they should be warned that a new vulnerability exists in the system.
A lot of people use Google Chrome or Firefox as their browser of choice, and it's easy to see why. They are updated constantly and have great features. However, a lot of people still stick to what they know and love - Internet Explorer. There are a lot of people out there that still use this browser, and they should be warned that a new vulnerability exists in the system.
 When you were a kid, did you ever ask your parents for a cool new toy only to have your request denied because you were in the habit of breaking everything? Your parents would point out your destructive habit and tell you, "This is why we can't have nice things." As an adult, the coolest toy is the Internet and hackers want to break it.
When you were a kid, did you ever ask your parents for a cool new toy only to have your request denied because you were in the habit of breaking everything? Your parents would point out your destructive habit and tell you, "This is why we can't have nice things." As an adult, the coolest toy is the Internet and hackers want to break it.
 There's nothing quite like the feeling of getting scammed, and the scammers of today love using technology to rip you off and leave you with that sinking scammy feeling. The best way to avoid scams is to be proactive and know what to look for. New to your list of scams to be on the look out for are fake apps.
There's nothing quite like the feeling of getting scammed, and the scammers of today love using technology to rip you off and leave you with that sinking scammy feeling. The best way to avoid scams is to be proactive and know what to look for. New to your list of scams to be on the look out for are fake apps.
 As technology grows more and more complex, the usefulness of your business's landline is declining. There are just plain better ways of communicating - cell phones are much more portable, and the Internet allows people to communicate with others while taking care of other work. One of the best ways to communicate over the Internet is by using Voice over Internet Protocol (VoIP), which provides the best of both worlds for those stuck in the landline age.
As technology grows more and more complex, the usefulness of your business's landline is declining. There are just plain better ways of communicating - cell phones are much more portable, and the Internet allows people to communicate with others while taking care of other work. One of the best ways to communicate over the Internet is by using Voice over Internet Protocol (VoIP), which provides the best of both worlds for those stuck in the landline age.
 It's the nature of trends for people to want to capitalize on them, which means that many sellers of what's trendy may have little experience working with the trends that they're selling. As a business looking to take advantage of the latest technology trends, it's important that you're not bamboozled by a smooth talking technology marketer with no depth.
It's the nature of trends for people to want to capitalize on them, which means that many sellers of what's trendy may have little experience working with the trends that they're selling. As a business looking to take advantage of the latest technology trends, it's important that you're not bamboozled by a smooth talking technology marketer with no depth.
 People in 1967 were fascinated with new technology. During this era, technology advanced so quickly in such a short amount of time that people looked in wonderment at the future and made wild predictions at what the 2000s would look like. How accurate were the predictions of the 1960's scientific community? Let's check in with Walter Cronkite to find out!
People in 1967 were fascinated with new technology. During this era, technology advanced so quickly in such a short amount of time that people looked in wonderment at the future and made wild predictions at what the 2000s would look like. How accurate were the predictions of the 1960's scientific community? Let's check in with Walter Cronkite to find out!
 Everyone dreads presentations, but for different reasons. Some people are just afraid of public speaking, or they are just overall unorganized. In the end, well designed presentations are essential for your company's success, whether they are given to clients or to your employees. Thankfully, there are ways to minimize the stress that giving a presentation can cause. One of the best ways to prepare a presentation is to use a Microsoft PowerPoint slideshow as an aid.
Everyone dreads presentations, but for different reasons. Some people are just afraid of public speaking, or they are just overall unorganized. In the end, well designed presentations are essential for your company's success, whether they are given to clients or to your employees. Thankfully, there are ways to minimize the stress that giving a presentation can cause. One of the best ways to prepare a presentation is to use a Microsoft PowerPoint slideshow as an aid.
However, it's very easy to fall into "PowerPoint Purgatory", a place filled with overburdened slideshows that last for hours on end. The amount of professionals who don't use PowerPoint effectively far outweigh those who do. Directive is here to help by providing you with some useful tips to make your presentations both easy for the presenter and for the audience!
 When we think of technology in terms of age, we often look at how long the machine has lasted for. Some machines from the mid-90's are still running, which makes them almost twenty years old. In terms of human life, that's not a very long time, but if you look at it in terms of quality working conditions, you'll find that these computers are kind of like dogs and cats. They may only be several years old, but in terms of actual age, their lifespan makes them much older than you realize.
When we think of technology in terms of age, we often look at how long the machine has lasted for. Some machines from the mid-90's are still running, which makes them almost twenty years old. In terms of human life, that's not a very long time, but if you look at it in terms of quality working conditions, you'll find that these computers are kind of like dogs and cats. They may only be several years old, but in terms of actual age, their lifespan makes them much older than you realize.
 2014 has been a year of technological advancement, but with any kind of advances such as these, there will always be those who want to steal the work of others. According to the Identity Theft Resource Center and , as of March this year, there have been 204 instances of data breaches this year alone. These affected companies are perfect examples of why web protection is important. Directive can provide you with this protection and peace of mind. Here are a few of the more unbelievable breaches, most of which could have been easily avoided.
2014 has been a year of technological advancement, but with any kind of advances such as these, there will always be those who want to steal the work of others. According to the Identity Theft Resource Center and , as of March this year, there have been 204 instances of data breaches this year alone. These affected companies are perfect examples of why web protection is important. Directive can provide you with this protection and peace of mind. Here are a few of the more unbelievable breaches, most of which could have been easily avoided.
 When life throws you for a loop and you are contracted with much more work than you are used to, perhaps it is time to upgrade your workstation. One of the simplest ways you can do this is by hooking up multiple monitors. With too many windows open, your desktop becomes cluttered and your workflow impeded. Stop getting lost in your work and hook up an extra screen today!
When life throws you for a loop and you are contracted with much more work than you are used to, perhaps it is time to upgrade your workstation. One of the simplest ways you can do this is by hooking up multiple monitors. With too many windows open, your desktop becomes cluttered and your workflow impeded. Stop getting lost in your work and hook up an extra screen today!
 Is your wireless router an older model? If it is, then you owe it to yourself to upgrade the latest model. Depending on your Internet connection, upgrading your wireless router may be the easiest way to increase your bandwidth. Next-gen routers also come with new easy-to-use security features that don't require passwords, making an upgrade worth the effort.
Is your wireless router an older model? If it is, then you owe it to yourself to upgrade the latest model. Depending on your Internet connection, upgrading your wireless router may be the easiest way to increase your bandwidth. Next-gen routers also come with new easy-to-use security features that don't require passwords, making an upgrade worth the effort.


















































![A Beginner's Guide to Facebook Advertising - Determining Your Facebook Advertising Budget [4 of 7]](http://autotask.directivesites.com/images/easyblog_articles/1877/b2ap3_large_b2ap3_thumbnail_FacebookBudget400.jpg)
![A Beginner's Guide to Facebook Advertising - Determining Your Facebook Advertising Budget [4 of 7]](https://autotask.directivesites.com/images/easyblog_articles/1877/b2ap3_large_b2ap3_thumbnail_FacebookBudget400.jpg)
![A Beginner's Guide to Facebook Advertising - Creating an AD [3 of 7]](/images/Step_1_-_Establish_and_create_your_facebook_business_page.png)













